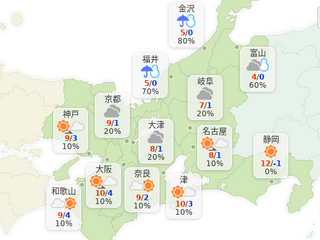
ACCOUNT_ID=`aws sts get-caller-identity | jq -r '.Account'`
cat << EOF > GreengrassV2InstallAssumeRolePolicy.json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::${ACCOUNT_ID}:root"
},
"Action": "sts:AssumeRole",
"Condition": {}
}
]
}
EOF
cat << EOF > GreengrassV2InstallPolicy.json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"greengrass:CreateDeployment",
"iot:AddThingToThingGroup",
"iot:AttachPolicy",
"iot:AttachThingPrincipal",
"iot:CreateJob",
"iot:CreateKeysAndCertificate",
"iot:CreatePolicy",
"iot:CreateRoleAlias",
"iot:CreateThing",
"iot:CreateThingGroup",
"iot:DescribeEndpoint",
"iot:DescribeRoleAlias",
"iot:DescribeThingGroup",
"iot:GetPolicy",
"iam:GetRole",
"iam:GetPolicy",
"iam:CreateRole",
"iam:PassRole",
"iam:CreatePolicy",
"iam:AttachRolePolicy"
],
"Resource": "*"
}
]
}
EOF
aws iam create-policy --policy-name GreengrassV2InstallPolicy --policy-document file://GreengrassV2InstallPolicy.json
aws iam create-role --role-name GreengrassV2InstallRole --assume-role-policy-document file://GreengrassV2InstallAssumeRolePolicy.json
aws iam attach-role-policy --policy-arn arn:aws:iam::${ACCOUNT_ID}:policy/GreengrassV2InstallPolicy --role-name GreengrassV2InstallRole